Load testing DNS servers and resolvers from your CLI
During my tenure at Jamf, where I was part of the team responsible for the development and maintenance of the DNS resolvers powering Secure DNS solutions (like Jamf Safe Internet), I often required some way to quickly execute simple to more advanced load tests of the DNS resolvers, preferably from my CLI.
While popular DNS load testing tools like DNSPerf and DNSBlast exist, I found they lacked the features I wanted, such as support for more advanced DNS protocols (like DNS over HTTPS, DNS over TLS, and DNS over QUIC), high concurrency of the load tests, randomization of the DNS queries, etc. This led me to create dnspyre, designed to address these gaps and provide a more flexible and comprehensive DNS load testing solution, purpose-built for command-line use.
dnspyre began as a fork of the dnstrace tool, a command-line benchmark for DNS servers. The original tool, written in Go, handled concurrent load generation well but was no longer actively maintained. Seeing its potential and wanting to add new features, I decided to fork dnstrace and create dnspyre.
dnspyre is a command-line DNS benchmark tool available for MacOS, Linux, and Windows. It supports DNS benchmarking across various protocols, including traditional DNS over UDP/TCP, DNS over HTTPS, DNS over TLS, and DNS over QUIC. The tool offers a range of configuration options, such as concurrency control, rate-limiting DNS queries, and connection sharing. These features allow users to tailor load tests for different scenarios.
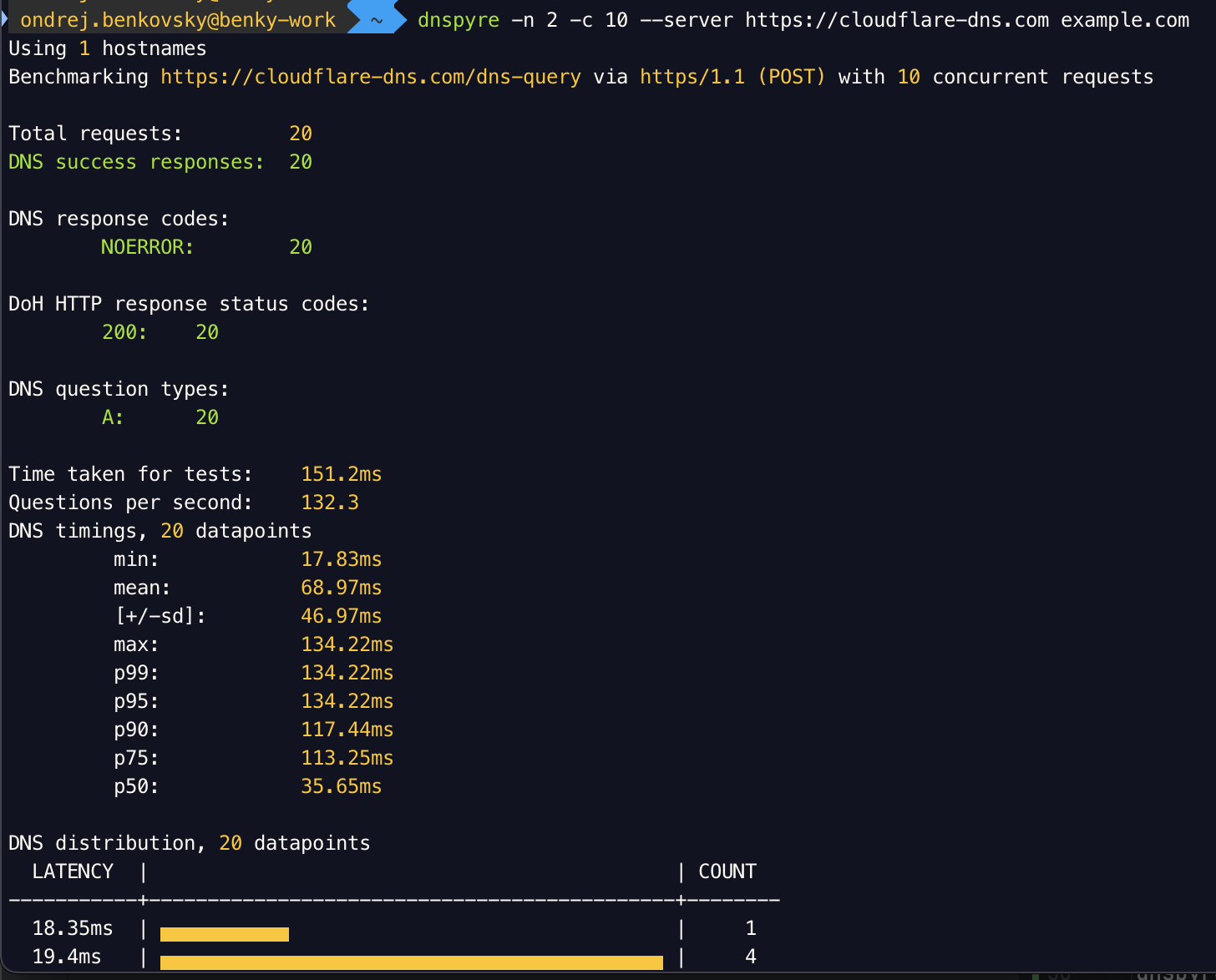
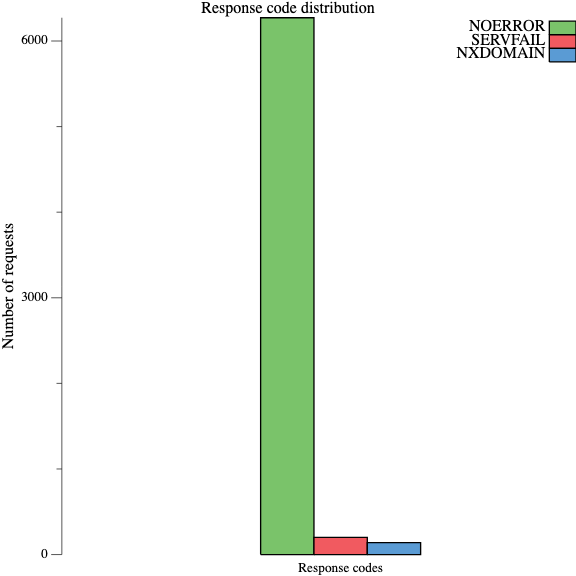
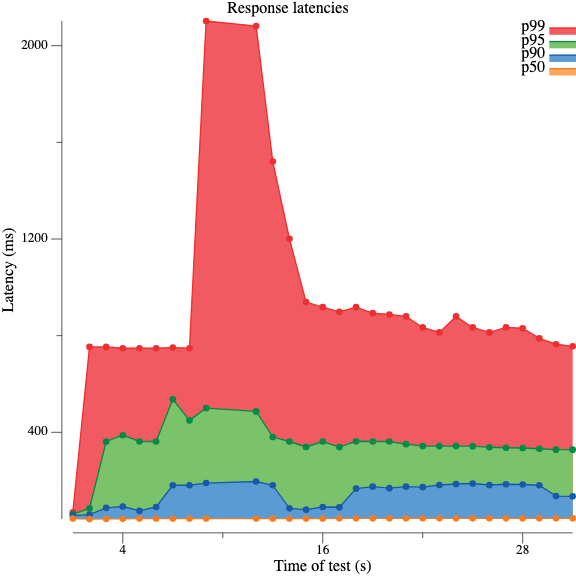
dnspyre also supports visualization of the results to make them easier to digest. It can plot graphs showing latency distribution as histograms and boxplots, visualize response codes as bar chart, or show the throughput of the benchmark as a line graph. See the documentation for more examples.
Development of dnspyre tool is still active, and if you have found any issues or have suggestions for improvements, please visit the project’s GitHub page to create a new issue or feel free to open a pull request.